The Methodology
The ITSRM2 methodology is a risk assessment methodology that helps organisations to assess the security risks associated with their IT systems and infrastructure. DIGIT proposes the IT Security Risk Management (ITSRM) Methodology to complement the EC's efforts for the protection of information systems that aims to protect the Commission's operations and third parties, including individuals, businesses, and Member States, from IT security incidents that can have a significant impact. The methodology provides a comprehensive approach that covers a wide range of potential risks and vulnerabilities, and it is based on established standards and guidelines, which helps ensure consistency and accuracy in risk assessments. It has many similarities and characteristics with the risk assessment process that is described in ISO/IEC 27005.
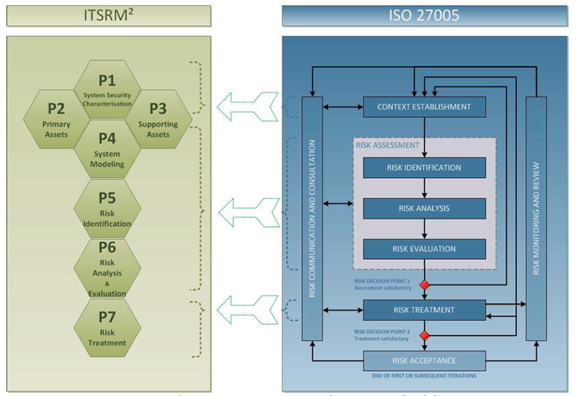
Figure 1: Mapping between ISO27005 & ITSRM2 Methodology
The first version of the ITSRM² methodology was published in March 2018, and it has undergone several updates since then.
Finally, there are two ways to conduct the risk assessment using the ITSRM2 either using the Excel tool provided by DIGIT or using the newly developed online tool GovSec.
Pros and Cons
From our experience using the ITSRM2 methodology over the past years and conducting many risk assessments for various European Commission Institutions and Agencies, we are listing below the top five pros and cons:
Pros
Comprehensive approach: The ITSRM2 methodology provides a comprehensive approach to IT security risk assessment and management, covering a wide range of potential risks and vulnerabilities.
Tailored to specific needs: The methodology can be tailored to meet the specific needs and requirements of different organisations, allowing for a customized approach to risk management.
Compliance: The methodology is aligned with various regulations and standards, such as ISO/IEC 27001, NIST helping organisations to comply with these requirements.
Risk prioritization: The methodology prioritizes risks based on their severity and likelihood, making it easier for organizations to focus on critical risks.
Continuous improvement: The methodology promotes continuous improvement by regularly assessing risks and updating mitigation measures.
Cons
Time-consuming: Implementing the ITSRM2 methodology can require significant time, effort, and resources.
Complex: The ITSRM2 methodology can be complex, with many different steps and processes to follow. This complexity can make it difficult for smaller organisations as well as for non-experts to understand and participate in the process.
Could be difficult to communicate: The results of risk assessments may be difficult to communicate and present effectively to stakeholders, which could limit their usefulness.
Cost: Implementing the ITSRM2 methodology can be expensive, particularly for smaller organizations or those with limited resources in terms of the cost of hiring dedicated experienced IT security professionals to conduct the assessment.
Limited applicability to non-IT risks: The ITSRM2 methodology is primarily designed to address IT risks. It may not be as applicable to other types of risks, such as operational, strategic and financial risks.
Conclusion
Overall, the ITSRM2 methodology is a valuable tool for improving an organisation's security posture and promoting ongoing risk awareness and management. However, organisations should carefully consider the benefits and the drawbacks before implementing the methodology to ensure that it is the right approach for their needs and resources.
Author: Vassilis Papachristos, Senior Information Security & Data Privacy Consultant

